Palo Alto PCNSA – Network Security Administrator

The Palo Alto PCNSA – Network Security Administrator Course also called Firewall Essentials: Configuration and Management EDU-210 is a training program that covers various aspects of cybersecurity, including topics such as advanced firewall configuration, threat prevention, URL filtering, WildFire analysis, and log management. Participants will gain practical skills in implementing these technologies to protect networks from attacks and threats. The course also focuses on enforcing security policies and responding to security incidents. The Course contributes to the preparation of the Palo Alto PCNSA – Network Security administrator Certification exam .
Course Objectives
Below is a summary of the main objectives of the Palo Alto PCNSA – Network Security Administrator Course :
- Deepen your understanding of next-generation firewall technologies, such as App-ID, Content-ID, and User-ID.
- Develop skills in configuring security policies and NAT.
- Explore URL filtering and threat prevention techniques.
- Dive deeper into network traffic monitoring and reporting strategies.
- Expand knowledge of network security best practices.
- Understand next-gen firewall technologies like App-ID and User-ID.
- Configure security policies, NAT, and URL filtering.
- Explore threat prevention, traffic monitoring, and reporting.
Course Certification
This course helps you prepare to take the:
PCNSA Exam – Palo Alto Networks Certified Network Security Administrator; Thist;
Course Outline
Cybersecurity Infrastructure and Configuration
Module 1 – Security Architecture Planning Resources
- Security platform overview
- Next-generation firewall architecture
- Zero Trust security model
- Firewall offerings
Module 2 – Infrastructure Device Configuration
- Security zones and interfaces
- Tap interfaces
- Virtual Wire interfaces
- Layer 2 interfaces
- Layer 3 interfaces
- Virtual routers
- Vlan interfaces
- Loopback interfaces
- Policy-based forwarding
Module 3 – Cybersecurity Policy
- Security policy fundamental concepts
- Security policy administration
- Network Address Translation
- Source NAT configuration
- Destination NAT configuration
Module 4 – Application Software Identification
- Application Identification (App-ID) overview
- Using App-ID in a Security policy
- Identifying unknown application traffic
- Updating App-ID
Module 5 – Anti-Virus, Anti-Spyware, and File-Blocking
- Content-ID overview
- Vulnerability Protection Security Profiles
- Antivirus Security Profiles
- Anti-Spyware Security Profiles
- File Blocking Profiles
- Attaching Security Profiles to Security policy rules
- Telemetry and threat intelligence
- Denial of service protection
Module 6 – Uniform Resource Locator Filtering
-
- URL Filtering Security Profiles
- Attaching URL Filtering Profiles
Cybersecurity Prevention and Countermeasures
Module 1 – Decryption and Certificate Management
- Decryption concepts
- Certificate management
- SSL forward proxy decryption
- SSL inbound inspection
- Other decryption topics
Module 2 – Virus Analysis and Mitigation
- Wildfire Virus Analysis and Mitigation
- Wildfire: concepts, configuring, managing, and reporting
Module 3 – End User Identification
- User-ID overview
- User mapping methods overview
- Configuring User-ID
- PAN-OS® integrated agent configuration
- Windows-based agent configuration
- Configuring group mapping
- User-ID and security policy
Module 4 – Remote Access Security
- Preparing the firewall for GlobalProtect
- Configuring the GlobalProtect portal
- Configuring the GlobalProtect gateway
- Configuring GlobalProtect agents
- Site to Site VPN Overview
- Configuring Site to Site tunnels
- IPsec troubleshooting
Module 5 – Security Monitoring and Reporting
- Dashboard, ACC, and monitor
- Log forwarding
- Syslog
- Configuring SNMP
Module 6 – Security Device High Availability
- High Availability Components and Operation
- Active/Passive HA Configuration
- Monitoring HA State
Course Mode
Instructor-Led Remote Live Classroom Training;
Trainers
Trainers s are Palo Alto Accredited Instructors and certified in other IT technologies, with years of practical experience in the sector and in Training.
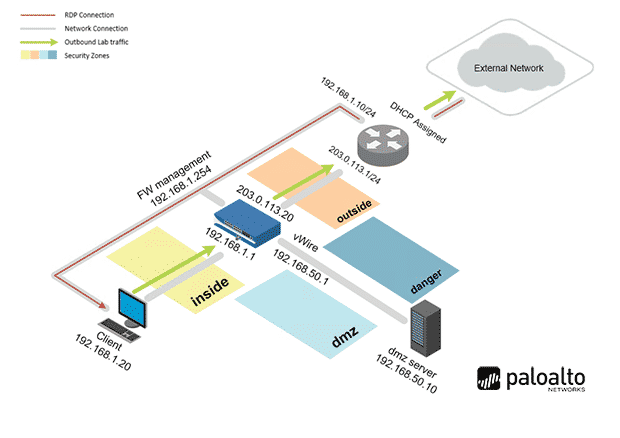
Lab Topology
For all types of delivery, the participant can access the equipment and actual systems in our laboratories or directly in international data centers remotely, 24/7. Each participant has access to implement various configurations, Thus immediately applying the theory learned. Below are some scenarios drawn from laboratory activities.
Course Details
Course Prerequisites
- Basic networking skills.
Course Duration
Intensive duration 5 days;
Course Frequency
Course Duration: 5 days (9.00 to 17.00) - Ask for other types of attendance.
Course Date
- Palo Alto PCNSA Course (Intensive Formula) – On request – 09:00 – 17:00
Steps to Enroll
Registration takes place by asking to be contacted from the following link, or by contacting the office at the international number +355 45 301 313 or by sending a request to the email info@hadartraining.com

