Microsoft Security Operations Analyst SC-200

The SC-200 Microsoft Security Operations Analyst course is designed to train participants in analyzing security operations for Microsoft solutions. The course covers topics such as monitoring, detecting and responding to threats, managing vulnerabilities, and analyzing security information, using tools such as Microsoft Azure Sentinel and Microsoft 365 Defender. The course curriculum extends beyond monitoring and detecting threats, including in-depth analysis of security incident response and vulnerability management. The course contributes to the preparation of the Microsoft Security Operations Analyst Associate Certification exam .
Course Objectives
Below is a summary of the main objectives of the Microsoft Security Operations Analyst SC-200 Course :
- Deepen your knowledge in analyzing security operations.
- Use Microsoft Azure Sentinel and Microsoft 365 Defender.
- Manage threat monitoring, detection and response.
- Manage vulnerabilities and analyze security information.
- Apply best practices in Microsoft operations security.
- Configure and manage security alerts and incidents in Microsoft Defender for Cloud.
- Investigate and respond to threats using advanced hunting and investigation techniques in Microsoft security solutions.
- Automate security tasks and workflows to enhance operational efficiency using Microsoft security tools and services.
Course Certification
This course helps you prepare to take the:
Exam SC-200 Microsoft Security Operations Analyst;
Course Outline
Mitigate threats to the Microsoft 365 environment by using Microsoft 365 Defender
- Investigate, respond, and remediate threats to Microsoft Teams, SharePoint Online, and OneDrive
- Investigate, respond, and remediate threats to email by using Microsoft Defender for Office 365
- Investigate and respond to alerts generated by data loss prevention (DLP) policies
- Investigate and respond to alerts generated by insider risk policies
- Discover and manage apps by using Microsoft Defender for Cloud Apps
- Identify, investigate, and remediate security risks by using Defender for Cloud Apps
Mitigate endpoint threats by using Microsoft Defender for Endpoint
- Manage data retention, alert notification, and advanced features
- Recommend attack surface reduction (ASR) for devices
- Respond to incidents and alerts
- Configure and manage device groups
- Identify devices at risk by using the Microsoft Defender Vulnerability Management
- Manage endpoint threat indicators
- Identify unmanaged devices by using device discovery
Mitigate identity threats
- Mitigate security risks related to events for Microsoft Entra ID
- Mitigate security risks related to Microsoft Entra Identity Protection events
- Mitigate security risks related to Active Directory Domain Services (AD DS) by using Microsoft Defender for Identity
Manage extended detection and response (XDR) in Microsoft 365 Defender
- Manage incidents and automated investigations in the Microsoft 365 Defender portal
- Manage actions and submissions in the Microsoft 365 Defender portal
- Identify threats by using Kusto Query Language (KQL)
- Identify and remediate security risks by using Microsoft Secure Score
- Analyze threat analytics in the Microsoft 365 Defender portal
- Configure and manage custom detections and alerts
Investigate threats by using audit features in Microsoft 365 Defender and Microsoft Purview
- Perform threat hunting by using unified audit log
- Perform threat hunting by using Content Search
- Use the guided hunting mode in Microsoft 365 Defender
- Use the advanced hunting mode in Microsoft 365 Defender
Implement and maintain cloud security posture management
- Assign and manage regulatory compliance policies, including Microsoft cloud security benchmark (MCSB)
- Improve the Microsoft Defender for Cloud secure score by applying recommended remediations
- Configure plans and agents for Microsoft Defender for Servers
- Configure and manage Microsoft Defender for DevOps
- Configure and manage Microsoft Defender External Attack Surface Management (EASM)
Configure environment settings in Microsoft Defender for Cloud
- Plan and configure Microsoft Defender for Cloud settings, including selecting target subscriptions and workspaces
- Configure Microsoft Defender for Cloud roles
- Assess and recommend cloud workload protection
- Enable plans for Microsoft Defender for Cloud
- Configure automated onboarding of Azure resources
- Connect compute resources by using Azure Arc
- Connect multi-cloud resources by using Environment settings
Respond to alerts and incidents in Microsoft Defender for Cloud
- Set up email notifications
- Create and manage alert suppression rules
- Design and configure workflow automation in Microsoft Defender for Cloud
- Remediate alerts and incidents by using Microsoft Defender for Cloud recommendations
- Manage security alerts and incidents
- Analyze Microsoft Defender for Cloud threat intelligence reports
Design and configure a Microsoft Sentinel workspace
- Plan a Microsoft Sentinel workspace
- Configure Microsoft Sentinel roles
- Design and configure Microsoft Sentinel data storage, including log types and log retention
Plan and implement the use of data connectors for ingestion of data sources in Microsoft Sentinel
- Identify data sources to be ingested for Microsoft Sentinel
- Configure and use Microsoft Sentinel connectors for Azure resources, including Azure Policy and diagnostic settings
- Configure Microsoft Sentinel connectors for Microsoft 365 Defender and Defender for Cloud
- Design and configure Syslog and Common Event Format (CEF) event collections
- Design and configure Windows security event collections
- Configure threat intelligence connectors
- Create custom log tables in the workspace to store ingested data
Manage Microsoft Sentinel analytics rules
- Configure the Fusion rule
- Configure Microsoft security analytics rules
- Configure built-in scheduled query rules
- Configure custom scheduled query rules
- Configure near-real-time (NRT) analytics rules
- Manage analytics rules from Content hub
- Manage and use watchlists
- Manage and use threat indicators
Perform data classification and normalization
- Classify and analyze data by using entities
- Query Microsoft Sentinel data by using Advanced Security Information Model (ASIM) parsers
- Develop and manage ASIM parsers
Configure security orchestration automated response (SOAR) in Microsoft Sentinel
- Create and configure automation rules
- Create and configure Microsoft Sentinel playbooks
- Configure analytic rules to trigger automation rules
- Trigger playbooks from alerts and incidents
Manage Microsoft Sentinel incidents
- Configure an incident generation
- Triage incidents in Microsoft Sentinel
- Investigate incidents in Microsoft Sentinel
- Respond to incidents in Microsoft Sentinel
- Investigate multi-workspace incidents
Use Microsoft Sentinel workbooks to analyze and interpret data
- Activate and customize Microsoft Sentinel workbook templates
- Create custom workbooks
- Configure advanced visualizations
Hunt for threats by using Microsoft Sentinel
- Analyze attack vector coverage by using MITRE ATT&CK in Microsoft Sentinel
- Customize content gallery hunting queries
- Create custom hunting queries
- Use hunting bookmarks for data investigations
- Monitor hunting queries by using Livestream
- Retrieve and manage archived log data
- Create and manage search jobs
Manage threats by using User and Entity Behavior Analytics
- Configure User and Entity Behavior Analytics settings
- Investigate threats by using entity pages
- Configure anomaly detection analytics rules
Course Mode
Instructor-Led Remote Live Classroom Training;
Trainers
Trainers are authorized Instructors in Microsoft and certified in other IT technologies, with years of hands-on experience in the industry and in Training.
Lab Topology
For all types of delivery, the participant can access the equipment and actual systems in our laboratories or directly in international data centers remotely, 24/7. Each participant has access to implement various configurations, Thus immediately applying the theory learned. Below are some scenarios drawn from laboratory activities.
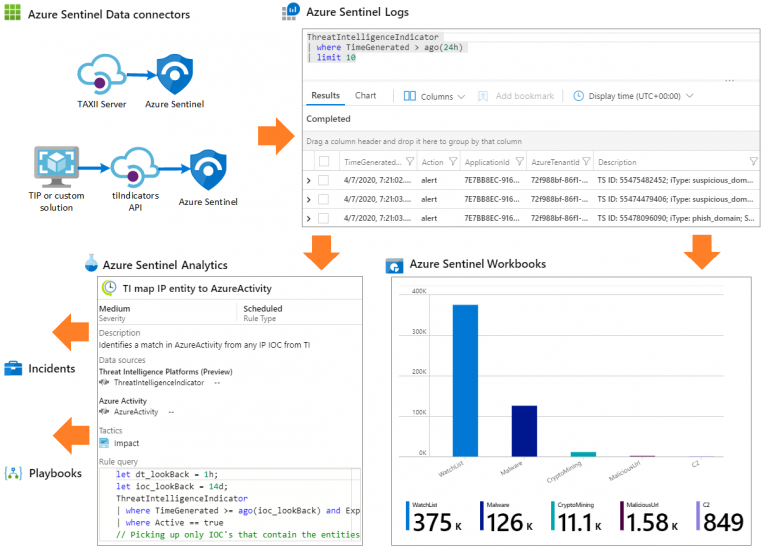
Course Details
Course Prerequisites
- Attendance at the Microsoft Security, Compliance, and Identity Fundamentals Course (SC-900) is recommended .
Course Duration
Intensive duration 4 days;
Course Frequency
Course Duration: 4 days (9.00 to 17.00) - Ask for other types of attendance.
Course Date
- Microsoft Security Operations Analyst course (Intensive Formula) – On request – 09:00 – 17:00
Steps to Enroll
Registration takes place by asking to be contacted from the following link, or by contacting the office at the international number +355 45 301 313 or by sending a request to the email info@hadartraining.com


