Microsoft Security, Compliance, and Identity Fundamentals SC-900

The SC-900 Microsoft Security, Compliance, and Identity Fundamentals course is an essential training program designed for participants who want to gain a solid understanding of the fundamental concepts of security, compliance, and identity in the Microsoft ecosystem. This course provides participants with a comprehensive overview of the different solutions and services that Microsoft offers to protect information, devices, and corporate infrastructure. During the course, participants will be introduced to the fundamental principles of cybersecurity and learn how Microsoft addresses these challenges through its technologies and services. Topics such as information protection, identity and access management, threat prevention, and regulatory compliance will be covered. Additionally, participants will explore the capabilities and best practices for using solutions such as Microsoft Azure, Microsoft 365, and Microsoft Defender. This course helps prepare for the Microsoft Security, Compliance, and Identity Fundamentals Certification exam .
Course Objectives
The following is a summary of the main objectives of the Microsoft Security, Compliance, and Identity Fundamentals Course :
- Gain an understanding of the basic concepts of security, compliance, and identity.
- Explore Microsoft solutions and services for protecting information and infrastructure.
- Learn the principles of identity and access management at Microsoft.
- Understand threat prevention and regulatory compliance strategies.
- Effectively use Microsoft Azure, Microsoft 365, and Microsoft Defender.
- Implement and manage security controls across Microsoft environments.
- Understand data protection and governance features within Microsoft 365 and Azure.
- Explore compliance management tools and strategies for meeting regulatory requirements.
Course Certification
This course helps you prepare to take the:
Exam SC-900 Microsoft Security, Compliance, and Identity Fundamentals;
Course Outline
Describe security and compliance concepts
- Describe the shared responsibility model
- Describe defense-in-depth
- Describe the Zero Trust model
- Describe encryption and hashing
- Describe Governance, Risk, and Compliance (GRC) concepts
Define identity concepts
- Define identity as the primary security perimeter
- Define authentication
- Define authorization
- Describe identity providers
- Describe the concept of directory services and Active Directory
- Describe the concept of federation
Describe function and identity types of Microsoft Entra ID
- Describe Microsoft Enter ID
- Describe types of identities
- Describe hybrid identity
Describe authentication capabilities of Microsoft Entra ID
- Describe the authentication methods
- Describe multi-factor authentication (MFA)
- Describe password protection and management capabilities
Describe access management capabilities of Microsoft Entra ID
- Describe Conditional Access
- Describe Microsoft Entra roles and role-based access control (RBAC)
Describe identity protection and governance capabilities of Microsoft Entra
- Describe Microsoft Entra ID Governance
- Describe access reviews
- Describe the capabilities of Microsoft Entra Privileged Identity Management
- Describe Entra ID Protection
- Describe Microsoft Entra Permissions Management
Describe core infrastructure security services in Azure
- Describe Azure distributed denial-of-service (DDoS) Protection
- Describe Azure Firewall
- Describe Web Application Firewall (WAF)
- Describe network segmentation with Azure virtual networks
- Describe network security groups (NSGs)
- Describe Azure Bastion
- Describe Azure Key Vault
Describe security management capabilities of Azure
- Describe Microsoft Defender for Cloud
- Describe Cloud Security Posture Management (CSPM)
- Describe how security policies and initiatives improve the cloud security posture
- Describe enhanced security features provided by cloud workload protection
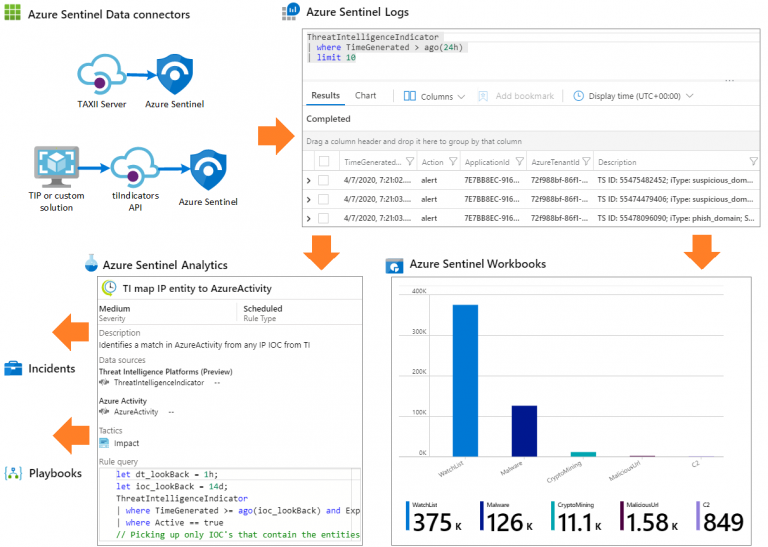
Describe capabilities of Microsoft Sentinel
- Define the concepts of security information and event management (SIEM) and security orchestration automated response (SOAR)
- Describe threat detection and mitigation capabilities in Microsoft Sentinel
Describe threat protection with Microsoft 365 Defender
- Describe Microsoft 365 Defender services
- Describe Microsoft Defender for Office 365
- Describe Microsoft Defender for Endpoint
- Describe Microsoft Defender for Cloud Apps
- Describe Microsoft Defender for Identity
- Describe Microsoft Defender Vulnerability Management
- Describe Microsoft Defender Threat Intelligence (Defender TI)
- Describe the Microsoft 365 Defender portal
Describe Microsoft Service Trust Portal and privacy principles
- Describe the Service Trust Portal offerings
- Describe the privacy principles of Microsoft
- Describe Microsoft Priva
Describe compliance management capabilities of Microsoft Purview
- Describe the Microsoft Purview compliance portal
- Describe Compliance Manager
- Describe the uses and benefits of compliance score
Describe information protection, data lifecycle management, and data governance capabilities of Microsoft Purview
- Describe the data classification capabilities
- Describe the benefits of Content explorer and Activity explorer
- Describe sensitivity labels and sensitivity label policies
- Describe data loss prevention (DLP)
- Describe records management
- Describe retention policies, retention labels, and retention label policies
- Describe unified data governance solutions in Microsoft Purview
Describe insider risk, eDiscovery, and audit capabilities in Microsoft Purview
- Describe insider risk management
- Describe eDiscovery solutions in Microsoft Purview
- Describe audit solutions in Microsoft Purview
Course Mode
Instructor-Led Remote Live Classroom Training;
Trainers
Trainers are authorized Instructors in Microsoft and certified in other IT technologies, with years of hands-on experience in the industry and in Training.
Lab Topology
For all types of delivery, the participant can access the equipment and actual systems in our laboratories or directly in international data centers remotely, 24/7. Each participant has access to implement various configurations, Thus immediately applying the theory learned. Below are some scenarios drawn from laboratory activities.
Course Details
Course Prerequisites
There are no prerequisites.
Course Duration
Intensive duration 1 days;
Course Frequency
Course Duration: 1 days (9.00 to 17.00) - Ask for other types of attendance.
Course Date
- Microsoft Security, Compliance, and Identity Fundamentals Course (Intensive Formula) – On request – 09:00 – 17:00
Steps to Enroll
Registration takes place by asking to be contacted from the following link, or by contacting the office at the international number +355 45 301 313 or by sending a request to the email info@hadartraining.com


