Cisco CyberOps Professional CBRCOR – Performing CyberOps Using Cisco Security Technologies

The CBRCOR Performing CyberOps Using Cisco Security Technologies course is the cornerstone of the CyberOPS Professional technology and certification path. It prepares the participant for the Cisco CyberOps Professional Certification Core exam (Exam 350-201). In this course, participants will acquire the skills, methods, and techniques for automating cybersecurity operations. The knowledge acquired in this course will prepare the participant for the role of information security analyst in a SOC (Security Operations Center) team. Participants will learn the fundamental and advanced concepts of cybersecurity and their application in real-world scenarios and how to leverage playbooks in formulating an incident response (IR). The course shows how to use automation for security using cloud platforms and a SecDevOps methodology. Participants will learn the techniques for detecting cyberattacks, analyzing threats, and formulating appropriate recommendations to improve cybersecurity in production contexts. The course contributes to the preparation of the Cisco DevNet Professional Certification exam (Exam 350-901) .
Course Objectives
The following is a summary of the main objectives of the CBRCOR Performing CyberOps Using Cisco Security Technologies Course :
- Understand SOC operations automation and the use of incident response playbooks.
- Apply advanced cybersecurity concepts in real-world scenarios.
- Utilize security automation on cloud platforms and adopt SecDevOps practices.
- Detect and analyze cyber threats to improve security.
- Prepare for the role of information security analyst in a SOC.
- Implement threat intelligence and use it to enhance incident response capabilities.
- Leverage SIEM (Security Information and Event Management) tools for efficient monitoring and threat detection.
- Develop and enforce security policies to ensure organizational compliance with cybersecurity standards.
Course Certification
This course helps you prepare to take the:
Exam 350-201 CBRCOR Performing CyberOps Using Cisco Security Technologies;
Course Outline
- Understanding Risk Management and SOC Operations
- Governance, Risk, and Compliance
- Security Regulatory Requirements
- Security Policy
- Protected Information
- Risk Analysis and Insurance
- SOC Services, Operations, and Automation
- SOC Service Models
- Understanding Analytical Processes and Playbooks
- Security Analytics
- SOC Playbook
- SOC Automation and Workflow
- Incident Response Concepts, Metrics, and Workflow
- Documenting Security Incidents in Cases
- Security Orchestration, Automation, and Response
- Cisco SecureX Orchestration Workflows
- Explore Cisco SecureX Orchestration
- Splunk Enterprise and Phantom Overview
- Explore Splunk Phantom Playbooks
- Investigating Packet Captures, Logs, and Traffic Analysis
- Identity Access Management Logs
- Artifacts and Traffic Streams in a Packet Capture
- Examine Cisco Firepower Packet Captures and PCAP Analysis
- Nextgen Firewall and IPS Logs
- Dissecting Suspicious Requests
- Network Traffic Analysis Using NetFlow Analytics
- Detecting and Enforcing DLP On-the-Wire
- Cisco AMP Architecture
- Cisco Web Security Appliance
- Network DNS Logs
- Cisco Email Security Appliance
- Email Security Logs (Not Detection-Based)
- Cisco Umbrella Reports
- Validate an Attack and Determine the Incident Response
- Investigating Endpoints and Appliance Logs
- Cisco ISE Monitoring, Reporting, and Alerting
- Cisco Advanced Malware Protection
- Cisco Threat Grid
- Submit a Malicious File to Cisco Threat Grid for Analysis
- Endpoint Logs from Non-Detection Sources
- DNS Server Logs
- Internet of Things
- Web Security Logs
- Endpoint Data Loss Protection
- Endpoint-Based Attack Scenario Referencing MITER ATTACK®
- Understanding Cloud Service Model Security Responsibilities
- Cloud Computing Evolution
- Cloud Service Models
- Security Responsibilities in the IaaS Service Model
- Security Responsibilities in the PaaS Service Model
- Security Responsibilities in the SaaS Service Model
- Cloud Deployment Models
- Key Security Controls in SaaS
- Cloud Access Security Broker
- Cisco CloudLock
- Cloud Security Regulations and References
- Understanding Enterprise Environment Assets
- Asset Management
- Remediating Vulnerabilities and the SOC
- Assessing Vulnerabilities
- Patch Management
- Data Storage and Protecting Data Privacy
- Multi-Factor Authentication
- Zero Trust Model
- Evaluate Assets in a Typical Enterprise Environment
- Implementing Threat Tuning
- Security Tuning Governance Policy
- Tuning Security Controls Rules, Filters, and Policies
- Determining If a Rule Is Defective
- Anatomy of a Snort Rule
- Explore Cisco Firepower NGFW Access Control Policy and Snort Rules
- Troubleshooting Detection Rules
- Recommending Scenarios for Tuning
- Threat Research and Threat Intelligence Practices
- Cyber Threat Intelligence Overview
- Cyber Threat Intelligence Lifecycle
- Cyber Threat Intelligence Data Sources
- Indicators of Compromise and Indicators of Attack
- Security Intelligence Reports
- Investigate IOCs from Cisco Talos Blog Using Cisco SecureX
- Cyber Attribution
- Cyber Threat Intelligence Tools
- Security Intelligence in a TIP Platform
- Using Indicator Analysis to Reveal Hidden Infections
- Explore the ThreatConnect Threat Intelligence Platform
- Track the TTPs of a Successful Attack Using a TIP
- Understanding APIs
- API Overview
- CSV, HTML, and XML Data Encoding
- JSON Data Encoding
- YAML Data Serialization Standard
- HTTP-Based APIs
- RESTful APIs vs. Non-RESTful APIs
- Cisco pxGrid
- HTTP-Based Authentication
- Postman
- Query Cisco Umbrella Using Postman API Client
- RESTCONF
- NETCONF
- Google RPC
- Data Modeling with YANG
- STIX and TAXII Specifications
- Role of APIs in Cisco Security Solutions
- Python Fundamentals
- Python Virtual Environments
- Fix a Python API Script
- Understanding SOC Development and Deployment Models
- Agile Methodology
- DevOps Practices and Principles
- Components of a CI/CD Pipeline
- Essential Windows and Linux CLI for Development and Operations
- Infrastructure as Code
- SOC Platform Development, Engineering, Operation, and Maintenance
- Create Basic Bash Scripts
- Performing Security Analytics and Reports in a SOC
- Security Data and Log Analytic Techniques
- Security Data Management Users
- Security Data with Log Management and Retention
- Security Data and Log Aggregations
- Security Information and Event Management
- Security Data and Log Analytics Automation
- Dashboards and Reports
- Malware Forensics Basics
- Malware Detection Tools
- Static Malware Analysis from Detection Tools
- Dynamic Malware Analysis from Sandbox Logs
- File Fingerprinting for Attribution
- Evading Detection
- Forensics Files
- Reverse Engineer Malware
- Threat Hunting Basics
- Proactive Threat Hunting Concepts
- Using MITER ATTACK® Framework for Threat Hunting
- Using CAPEC to Hunt for Weaknesses in Applications
- Evaluating Security Posture and Gaps in Controls Using MITER ATTACK®
- Threat Hunting Case Study
- Perform Threat Hunting
- Performing Incident Investigation and Response
- Threat Modeling
- Indicators of Compromise and Indicators of Attack
- Attack Campaigns, Tactics, Techniques, and Procedures
- Sequence of Events During an Attack Based on Analysis of Traffic Patterns
- Steps to Investigate the Common Types of Cases
- IRT Concepts and Actions
- Tool-Based Mitigation and Gaps
- Steps to Investigate Potential Data Loss
- Conduct an Incident Response
- Lessons Learned
Laboratory Activities
- Explore Cisco SecureX Orchestration
- Explore Splunk Phantom Playbooks
- Examine Cisco Firepower Packet Captures and PCAP Analysis
- Validate an Attack and Determine the Incident Response
- Submit a Malicious File to Cisco Threat Grid for Analysis
- Endpoint-Based Attack Scenario Referencing MITER ATTACK®
- Evaluate Assets in a Typical Enterprise Environment
- Explore Cisco Firepower NGFW Access Control Policy and Snort Rules
- Investigate IOCs from Cisco Talos Blog Using Cisco SecureX
- Explore the ThreatConnect Threat Intelligence Platform
- Track the TTPs of a Successful Attack Using a TIP
- Query Cisco Umbrella Using Postman API Client
- Fix a Python API Script
- Create Basic Bash Scripts
- Reverse Engineer Malware
- Perform Threat Hunting
Course Mode
Instructor-Led Remote Live Classroom Training;
Trainers
Trainers are Cisco Official Instructors and certified in other IT technologies, with years of hands-on experience in the industry and in Training.
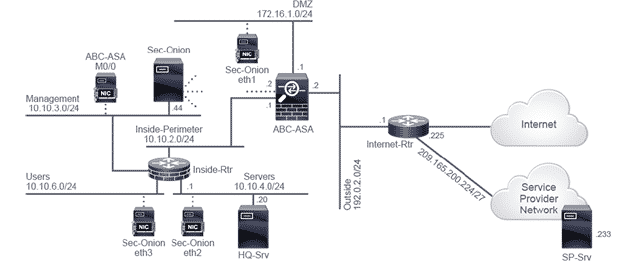
Lab Topology
For all types of delivery, the Trainee can access real Cisco equipment and systems in our laboratories or directly at the Cisco data centers remotely 24 hours a day. Each participant has access to implement the various configurations thus having a practical and immediate feedback of the theoretical concepts.
Here are some Cisco Labs network topologies available:
Course Details
Course Prerequisites
- Attendance at the Cisco Cybersecurity Operations Associate Course is recommended .
Course Duration
Intensive duration 5 days
Course Frequency
Course Duration: 5 days (9.00 to 17.00) - Ask for other types of attendance.
Course Date
-
- Cisco CBRCOR Course (Intensive Formula) – On request – 9:00 – 17:00
Steps to Enroll
Registration takes place by asking to be contacted from the following link, or by contacting the office at the international number +355 45 301 313 or by sending a request to the email info@hadartraining.com


