Cisco CBROPS – Understanding Cisco Cybersecurity Operations Fundamentals

The CBROPS Understanding Cisco Cybersecurity Operations Fundamentals Course is a highly specialized training program aimed at those who wish to acquire essential skills in cybersecurity operations. During the course, participants will have the opportunity to learn the basics of networks, security systems and cyber threats, as well as best practices for preventing, detecting and responding to cyber attacks. Participants will be guided through a series of theoretical and practical lessons covering topics such as network security, threat analysis, security incident management and digital investigation techniques. Additionally, you will be introduced to the various tools and technologies used in cybersecurity operations, such as intrusion prevention systems, firewalls, and network traffic analysis tools. The course is aimed at both beginners in the field of cybersecurity and those who already work in IT and wish to expand their knowledge and skills in the sector. Participants will learn how to protect IT infrastructures, detect and prevent attacks, and effectively respond to security incidents. The course helps prepare for the Cisco CyberOps Associate Certification exam (Exam 200-201 ).
Course Objectives
Below is a summary of the main objectives of the CBROPS Understanding Cisco Cybersecurity Operations Fundamentals course :
- Learning the basics of networks and security systems.
- Knowledge of cyber threats and prevention techniques.
- Introduction to network security and threat analysis.
- Security incident management and digital investigation techniques.
- Familiarity with cybersecurity tools and technologies.
- Understanding security monitoring tools and techniques.
- Implementing security policies and procedures.
- Developing skills in cybersecurity risk management and mitigation strategies
Course Certification
This course helps you prepare to take the:
Exam 200-201 CBROPS Cisco Certified CyberOps Associate CyberOps;
Course Outline
- Defining the Security Operations Center
- Introduction
- Types of Security Operations Centers
- SOC Analyst Tools
- Data Analytics
- Hybrid Installations: Automated Reports, Anomaly Alerts
- Staffing an Effective Incident Response Team
- Roles in a Security Operations Center
- Developing Key Relationships with External Resources
- Understanding Network Infrastructure and Network Security Monitoring Tools
- Introduction
- NAT Fundamentals
- Packet Filtering with ACLs
- ACLs with the Established Option
- Access Control Models
- Authentication, Authorization, and Accounting
- Load Balancing
- Network-Based Malware Protection
- Network Security Monitoring Tools
- Exploring Data Type Categories
- Introduction
- Network Security Monitoring Data
- Network Security Monitoring Data Types
- Security Information and Event Management Systems
- Security Orchestration, Automation, and Response
- Security Onion Overview
- Full Packet Capture
- Packet Captures
- Packet Capture Using Tcpdump
- Session Data
- Transaction Data
- Alert Data
- Other Data Types
- Correlating NSM Data
- Information Security Confidentiality, Integrity, and Availability
- Personally Identifiable Information
- Regulatory Compliance
- Intellectual Property
- Use NSM Tools to Analyze Data Categories
- Understanding Basic Cryptography Concepts
- Introduction
- Impact of Cryptography on Security Investigations
- Cryptography Overview
- Hash Algorithms
- Encryption Overview
- Cryptanalysis
- Symmetric Encryption Algorithms
- Asymmetric Encryption Algorithms
- Diffie-Hellman Key Agreement
- Use Case: SSH
- Digital Signatures
- PKI Overview
- PKI Operations
- Use Case: SSL/TLS
- Cipher Suite
- Key Management
- NSA Suite B
- Explore Cryptographic Technologies
- Understanding Common TCP/IP Attacks
- Introduction
- Address Resolution Protocol
- Legacy TCP/IP Vulnerabilities
- IP Vulnerabilities
- ICMP Vulnerabilities
- TCP Vulnerabilities
- UDP Vulnerabilities
- Attack Surface and Attack Vectors
- Reconnaissance Attacks
- Access Attacks
- Man-in-the-Middle Attacks
- Denial of Service and Distributed Denial of Service
- Reflection and Amplification Attacks
- Spoofing Attacks
- DHCP Attacks
- Explore TCP/IP Attacks
- Understanding Endpoint Security Technologies
- Introduction
- Host-Based Personal Firewall
- Host-Based Antivirus
- Host Intrusion Prevention System
- Application Whitelists and Blacklists
- Host-Based Malware Protection
- Sandboxing
- File Integrity Checking
- Explore Endpoint Security
- Understanding Incident Analysis in a Threat-Centric SOC
- Introduction
- Classic Kill Chain Model Overview
- Kill Chain Phase : Reconnaissance
- Kill Chain Phase : Weaponization
- Kill Chain Phase : Delivery
- Kill Chain Phase : Exploitation
- Kill Chain Phase : Installation
- Kill Chain Phase : Command-and-Control
- Kill Chain Phase : Actions on Objectives
- Applying the Kill Chain Model
- Diamond Model Overview
- Applying the Diamond Model
- MITRE ATTACK™ Framework
- Investigate Hacker Methodology
- Identifying Resources for Hunting Cyber Threats
- Introduction
- Cyber-Threat Hunting Concepts
- Hunting Maturity Model
- Cyber Threat Hunting Cycle
- Common Vulnerability Scoring System
- CVSS vScoring
- CVSS vExample
- Hot Threat Dashboard
- Publicly Available Threat Awareness Resources
- Other External Threat Intelligence Sources and Feeds Reference
- Security Intelligence
- Threat Analytic Systems
- Security Tools Reference
- Hunt Malicious Traffic
- Understanding Event Correlation and Normalization
- Introduction
- Event Sources
- Evidence
- Chain of Custody
- Security Data Normalization
- Event Correlation
- Other Security Data Manipulation
- Correlate Event Logs, PCAPs, and Alerts of an Attack
- Identifying Common Attack Vectors
- Introduction
- DNS Operations
- Recursive DNS Query
- Dynamic DNS
- HTTP Operations
- HTTPS Operations
- HTTP/ Operations
- SQL Operations
- SMTP Operations
- Web Scripting
- Obfuscated JavaScript
- Shellcode and Exploits
- Common Metasploit Payloads
- Directory Traversal
- SQL Injection
- Cross-Site Scripting
- Punycode
- DNS Tunneling
- Pivoting
- HTTP Cushioning
- Gaining Access Via Web-Based Attacks
- Exploit Kits
- Emotet Advanced Persistent Threat
- Investigate Browser-Based Attacks
- Identifying Malicious Activity
- Introduction
- Understanding the Network Design
- Zero Trust Model
- Identifying Possible Threat Actors
- Log Data Search
- System Logs
- Windows Event Viewer
- Firewall Log
- DNS Log
- Web Proxy Log
- Email Proxy Log
- AAA Server Log
- Next Generation Firewall Log
- Applications Log
- NetFlow
- NetFlow as a Security Tool
- Network Behavior Anomaly Detection
- Data Loss Detection Using NetFlow Example
- DNS Risk and Mitigation Tool
- IPS Evasion Techniques
- The Onion Router
- Gaining Access and Control
- Peer-to-Peer Networks
- Encapsulation
- Altered Disk Image
- Analyze Suspicious DNS Activity
- Explore Security Data for Analysis
- Identifying Patterns of Suspicious Behavior
- Introduction
- Network Baselining
- Identifying Anomalies and Suspicious Behaviors
- PCAP Analysis
- Delivery
- Investigate Suspicious Activity Using Security Onion
- Conducting Security Incident Investigations
- Introduction
- Security Incident Investigation Procedures
- Threat Investigation Example: China Chopper Remote Access Trojan
- Investigate Advanced Persistent Threats
- Using a Playbook Model to Organize Security Monitoring
- Introduction
- Security Analytics
- Playbook Definition
- What Is in a Play?
- Playbook Management System
- Explore SOC Playbooks
- Understanding SOC Metrics
- Introduction
- Security Data Aggregation
- Time to Detection
- Security Controls Detection Effectiveness
- SOC Metrics
- Understanding SOC Workflow and Automation
- Introduction
- SOC WMS Concepts
- Incident Response Workflow
- SOC WMS Integration
- SOC Workflow Automation Example
- Describing Incident Response
- Introduction
- Incident Response Planning
- Incident Response Life Cycle
- Incident Response Policy Elements
- Incident Attack Categories
- Reference: US-CERT Incident Categories
- Regulatory Compliance Incident Response Requirements
- CSIRT Categories
- CSIRT Framework
- CSIRT Incident Handling Services
- Understanding the Use of VERIS
- Introduction
- VERIS Overview
- SPRING Incidents Structure
- True A’s
- SPRING Records
- VERIS Community Database
- Verizon Data Breach Investigations Report and Cisco Annual Security Report
- Understanding Windows Operating System Basics
- Introduction
- Windows Operating System History
- Windows Operating System Architecture
- Windows Processes, Threads, and Handles
- Windows Virtual Memory Address Space
- Windows Services
- Windows File System Overview
- Windows File System Structure
- Windows Domains and Local User Accounts
- Windows GUI
- Run as Administrator
- Windows CLI
- Windows PowerShell
- Windows net Command
- Controlling Startup Services and Executing System Shutdown
- Controlling Services and Processes
- Monitoring System Resources
- Windows Boot Process
- Windows Networking
- Windows netstat Command
- Accessing Network Resources with Windows
- Windows Registry
- Windows Management Instrumentation
- Common Windows Server Functions
- Common Third-Party Tools
- Explore the Windows Operating System
- Understanding Linux Operating System Basics
- Introduction
- History and Benefits of Linux
- Linux Architecture
- Linux File System Overview
- Basic File System Navigation and Management Commands
- File Properties and Permissions
- Editing File Properties
- Root and Sudo
- Disks and File Systems
- System Initialization
- Emergency/Alternate Startup Options
- Shutting Down the System
- System Processes
- Interacting with Linux
- Linux Command Shell Concepts
- Piping Command Output
- Other Useful Command-Line Tools
- Overview of Secure Shell Protocol
- Networking
- Managing Services in SysV Environments
- Viewing Running Network Services
- Name Resolution: DNS
- Testing Name Resolution
- Viewing Network Traffic
- Configuring Remote Syslog
- Running Software on Linux
- Executables vs. Interpreters
- Using Package Managers to Install Software in Linux
- System Applications
- Lightweight Directory Access Protocol
- Explore the Linux Operating System
Laboratory Activities
- Configure the Initial Collaboration Lab Environment
- Use NSM Tools to Analyze Data Categories
- Explore Cryptographic Technologies
- Explore TCP/IP Attacks
- Explore Endpoint Security
- Investigate Hacker Methodology
- Hunt Malicious Traffic
- Correlate Event Logs, PCAPs, and Alerts of an Attack
- Investigate Browser-Based Attacks
- Analyze Suspicious DNS Activity
- Explore Security Data for Analysis
- Investigate Suspicious Activity Using Security Onion
- Investigate Advanced Persistent Threats
- Explore SOC Playbooks
- Explore the Windows Operating System
- Explore the Linux Operating System
Course Mode
Instructor-Led Remote Live Classroom Training;
Trainers
Trainers are authorized Instructors in CISCO certified and in other IT technologies, with years of hands-on experience in the industry and in Training.
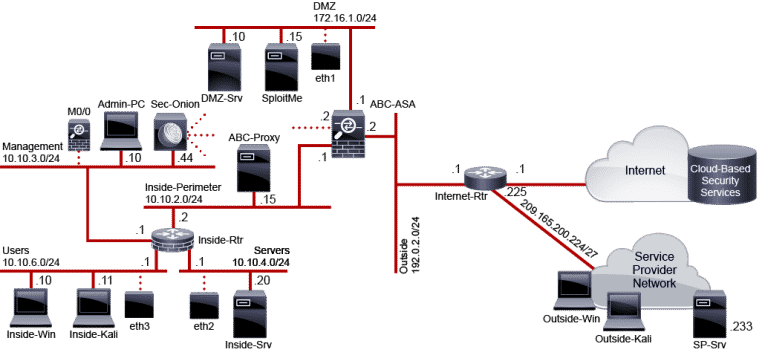
Lab Topology
For all types of delivery, the participant can access the equipment and actual systems in our laboratories or directly in international data centers remotely, 24/7. Each participant has access to implement various configurations, Thus immediately applying the theory learned. Below are some scenarios drawn from laboratory activities.
Course Details
Course Prerequisites
No Prerequisites.
Course Duration
Intensive duration 5 days;
Course Frequency
Course Duration: 5 days (9.00 to 17.00) - Ask for other types of attendance.
Course Date
- Developing solutions for CBROPS course (Intensive Formula) – On request – 09:00 – 17:00
Steps to Enroll
Registration takes place by asking to be contacted from the following link, or by contacting the office at the international number +355 45 301 313 or by sending a request to the email info@hadartraining.com


