CCNP Security SCOR – Implementing and Operating Cisco Security Core Technologies

The SCOR Implementing and Operating Cisco Security Core Technologies Course represents the fundamental pillar of the Security technological and certification path and prepares the participant for the Core exam of the CCNP Security Certification (Exam 350-701). The main objective of the course is to provide participants with the knowledge and skills necessary to implement and manage Cisco security technologies in a wide range of environments. During the course, participants will gain an in-depth understanding of cybersecurity principles and techniques, including endpoint management, identity and access management, firewall and VPN management, advanced threat management, and of security systems. Additionally, participants will learn to configure and manage Cisco security technologies, such as ASA, Firepower, VPN, IPS, and AMP. The course contributes to the preparation of the CCNP Security Certification exam (Exam 350-701) .
Course Objectives
The main objectives of the SCOR Implementing and Operating Cisco Security Core Technologies course are:
- Provide an in-depth understanding of cybersecurity principles.
- Manage and configure Cisco security technologies such as ASA, Firepower, and VPN.
- Acquire skills in identity and access management.
- Learn more about managing advanced threats and security systems.
- Prepare for the CCNP Security SCOR Certification exam.
- Dive deep into security analytics tools and techniques, leveraging data insights for threat detection, incident response, and continuous security monitoring
- Learn to design and deploy secure network architectures using Cisco technologies, focusing on segmentation, micro-segmentation, and zero-trust security models.
- Gain expertise in understanding and implementing security standards and regulatory compliance frameworks such as GDPR, HIPAA, and PCI DSS within Cisco security solutions.
Course Certification
This course helps you prepare to take the:
Exam 350-701 SCOR Implementing and Operating Cisco Security Core TechnologieS
Course Outline
- Describing Information Security Concepts
- Describing Common TCP/IP Attacks
- Describing Common Network Application Attacks
- Describing Common Endpoint Attacks*
- Describing Network Security Technologies
- Deploying Cisco ASA Firewall
- Deploying Cisco Firepower Next-Generation Firewall
- Deploying Email Content Security
- Deploying Web Content Security
- Deploying Cisco Umbrella*
- Explaining VPN Technologies and Cryptography
- Introducing Cisco Secure Site-to-Site VPN Solutions
- Deploying Cisco IOS VTI-Based Point-to-Point IPsec VPNs
- Deploying Point-to-Point IPsec VPNs on the Cisco ASA and Cisco Firepower NGFW
- Introducing Cisco Secure Remote Access VPN Solutions
- Deploying Remote Access SSL VPNs on the Cisco ASA and Cisco Firepower NGFW
- Explaining Cisco Secure Network Access Solutions
- Describing 802.1X Authentication
- Configuring 802.1X Authentication
- Describing Endpoint Security Technologies*
- Deploying Cisco Advanced Malware Protection (AMP) for Endpoints*
- Introducing Network Infrastructure Protection*
- Deploying Control Plane Security Controls*
- Deploying Layer 2 Data Plane Security Controls*
- Deploying Layer 3 Data Plane Security Controls*
- Deploying Management Plane Security Controls*
- Deploying Traffic Telemetry Methods*
- Deploying Cisco Stealthwatch Enterprise*
- Describing Cloud and Common Cloud Attacks*
- Securing the Cloud*
- Deploying Cisco Stealthwatch Cloud*
- Describing Software-Defined Networking (SDN*)
Laboratory Activities
- Configure Network Settings and NAT on Cisco ASA
- Configure Cisco ASA Access Control Policies
- Configure Cisco Firepower NGFW NAT
- Configure Cisco Firepower NGFW Access Control Policy
- Configure Cisco Firepower NGFW Discovery and IPS Policy
- Configure Cisco NGFW Malware and File Policy
- Configure Listener, Host Access Table (HAT), and Recipient Access Table (RAT) on Cisco Email Security Appliance (ESA)
- Configure Mail Policies
- Configure Proxy Services, Authentication, and HTTPS Decryption
- Enforce Acceptable Use Control and Malware Protection
- Examine the Umbrella Dashboard
- Examine Cisco Umbrella Investigate
- Explore DNS Ransomware Protection by Cisco Umbrella
- Configure Static VTI Point-to-Point IPsec IKEv2 Tunnel
- Configure Point-to-Point VPN between the Cisco ASA and Cisco Firepower NGFW
- Configure Remote Access VPN on the Cisco Firepower NGFW
- Explore Cisco AMP for Endpoints
- Perform Endpoint Analysis Using AMP for Endpoints Console
- Explore File Ransomware Protection by Cisco AMP for Endpoints Console
- Explore Cisco Stealthwatch Enterprise v6.9.3
- Explore Cognitive Threat Analytics (CTA) in Stealthwatch Enterprise v7.0
- Explore the Cisco Cloudlock Dashboard and User Security
- Explore Cisco Cloudlock Application and Data Security
- Explore Cisco Stealthwatch Cloud
- Explore Stealthwatch Cloud Alert Settings, Watchlists, and Sensors
Course Mode
Instructor-Led Remote Live Classroom Training;
Trainers
Trainers are CISCO Official Instructors and certified in other IT technologies, with years of hands-on experience in the industry and in Training.
Lab Topology
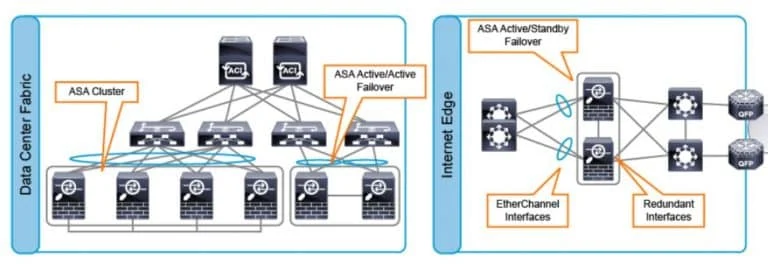
For all types of delivery, the participant can access the equipment and actual systems in our laboratories or directly in international data centers remotely, 24/7. Each participant has access to implement various configurations, Thus immediately applying the theory learned. Below are some scenarios drawn from laboratory activities.
Course Details
Course Prerequisites
Participation in the Cisco CCNA Course and the Cisco Cybersecurity Course is recommended .
Course Duration
Extensive Duration 60 Hours; Intensive duration 5 days;
Course Frequency
Course Duration: 5 days (9.00 to 17.00) - Ask for other types of attendance.
Course Date
Cisco SCOR Course (Intensive Formula) – On Request – 09:00 – 17:00
Steps to Enroll
Registration takes place by asking to be contacted from the following link, or by contacting the office at the international number +355 45 301 313 or by sending a request to the email info@hadartraining.com


