Check Point CCSA Security Administrator

The Check Point Security Administration (CCSA) Course provides the skills and knowledge of the fundamental concepts necessary to configure the core technologies offered by the Check Point ecosystem. During the course, participants will learn how to implement, configure and manage a Check Point security solution to protect networks from cyber threats. The course covers a wide range of topics, including installing and configuring Check Point software, managing users and security objects, configuring access control, configuring security rules, managing connections VPN and much more. The course helps prepare for the Check Point Security Administrator (CCSA) Certification exam .
Course Objectives
Below is a summary of the main objectives of the Check Point CCSA Security Administrator Course :
- Installation and configuration of Check Point network security software.
- Effectively manage users and security objects in Check Point environments.
- Detailed configuration of access control and security rules.
- In-depth analysis of VPN connection management and strategies against cyber threats.
- Explore Check Point’s advanced capabilities for protecting corporate networks.
- Learn to troubleshoot and resolve common issues within Check Point environments for maintaining system stability.
- Develop skills in configuring and managing Check Point’s threat prevention features to counteract emerging security threats.
- Gain practical experience through hands-on labs focusing on Check Point’s security management and monitoring tools.
Course Certification
This course helps you prepare to take the:
Check Point Security Administrator (CCSA) exam;
Course Outline
- Describe the primary components of a Check Point Three-Tier Architecture and explain how they work together in the Check Point environment.
- Explain how communication is secured and how traffic is routed in the Check Point environment.
- Describe the basic functions of the Gaia operating system.
- Identify the basic workflow to install Security Management Server and Security Gateway for a single-domain solution.
- Create SmartConsole objects that correspond to the organization’s topology for use in policies and rules.
- Identify the tools available to manage Check Point licenses and contracts, including their purpose and use.
- Identify features and capabilities that enhance the configuration and management of the Security Policy.
- Explain how policy layers affect traffic inspection.
- Articulate how Network Address Translation affects traffic.
- Describe how to configure manual and automatic Network Address Translation (NAT).
- Demonstrate an understanding of Application Control & URL Filtering and Autonomous Threat Prevention capabilities and how to configure these solutions to meet an organization’s security requirements.
- Articulate how pre-shared keys and certificates can be configured to authenticate with third-party and externally managed VPN Gateways.
- Describe how to analyze and interpret VPN tunnel traffic.
- Configure logging parameters.
- Use predefined and custom queries to filter log results.
- Identify how to monitor the health of supported Check Point hardware using the Gaia Portal and the command line.
- Describe the different methods for backing up Check Point system information and discuss best practices and recommendations for each method.
Laboratory Activities
- Deploying SmartConsole
- Installing a Security Management Server
- Installing a Security Gateway
- Configuring Objects in SmartConsole
- Establishing Secure Internal Communication
- Managing Administrator Access
- Managing Licenses
- Creating a Security Policy
- Configuring Order Layers
- Configuring a Shared Inline Layer
- Configuring NAT
- Integrating Security with a Unified Policy
- Elevating Security with Autonomous Threat Prevention
- Configuring a Locally Managed Site-to-Site VPN
- Elevating Traffic View
- Monitoring System States
- Maintaining the Security Environment
Course Mode
Instructor-Led Remote Live Classroom Training;
Trainers
Trainers are Authorized Check Point Instructors and certified in other IT technologies, with years of practical experience in the sector and in training.
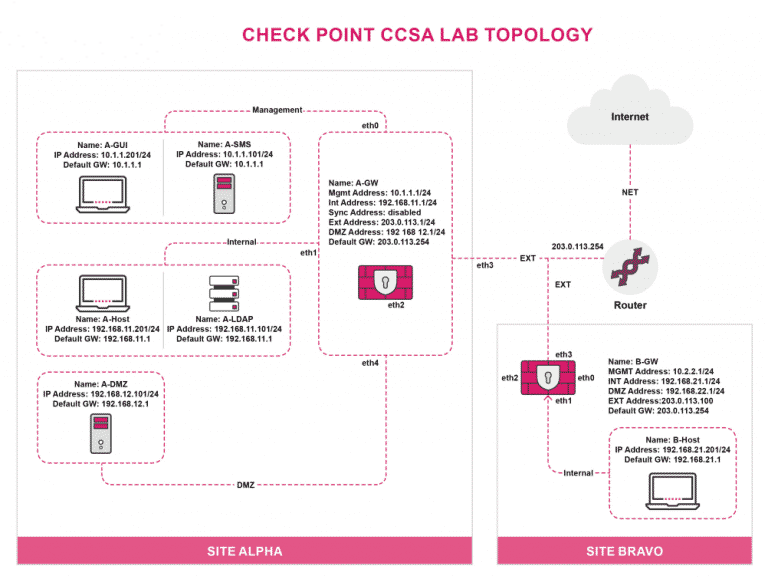
Lab Topology
For all types of delivery, the participant can access the equipment and actual systems in our laboratories or directly in international data centers remotely, 24/7. Each participant has access to implement various configurations, Thus immediately applying the theory learned. Below are some scenarios drawn from laboratory activities.
Course Details
Course Prerequisites
- Participants must have a basic knowledge of the fundamentals of Networking and Windows/Linux systems.
Course Duration
Intensive duration 3 days;
Course Frequency
Course Duration: 3 days (9.00 to 17.00) - Ask for other types of attendance.
Course Date
- Check Point CCSA Course (Intensive Formula) – On request – 09:00 – 17:00
Steps to Enroll
Registration takes place by asking to be contacted from the following link, or by contacting the office at the international number +355 45 301 313 or by sending a request to the email info@hadartraining.com


