CCNP Security SWSA – Securing the Web with Cisco Web Security Appliance

The SWSA Securing the Web with Cisco Web Security Appliance Course is part of the Cisco CCNP Security track. This course delves into the implementation and management of the Cisco Web Security Appliance (WSA) solution (by Cisco Talos) to provide advanced web traffic protection and counteract security threats. This platform allows the distribution of proxy services, implementation of authentication, management of policies for controlling HTTP and HTTPS traffic, the implementation of access control policies up to anti-malware capabilities, data loss prevention and administration of Cisco WSA solutions. The Course contributes to the preparation of the Cisco CCNP Security SWSA Certification exam (Exam 300-725) .
Course Objectives
The following is a summary of the main objectives of the SWSA Securing the Web with Cisco Web Security Appliance Course :
- Implementation and management of the Cisco Web Security Appliance (WSA) solution.
- Deploying proxy services and implementing authentication.
- Manage policies for controlling HTTP and HTTPS traffic.
- Implement access control policies and anti-malware capabilities.
- Data loss prevention and administration of Cisco WSA solutions.
- Optimize web security performance: Enhance efficiency and resource utilization for web protection.
- Integrate advanced threat detection: Use sophisticated methods to identify and mitigate web-based threats.
- Apply best practices for web security management: Ensure effective and secure deployment of Cisco WSA solutions.
Course Certification
This course helps you prepare to take the:
Exam 300-725 SWSA Securing the Web with Cisco Web Security Appliance;
Course Outline
- Describing Cisco WSA
- Technology Use Case
- Cisco WSA Solution
- Cisco WSA Features
- Cisco WSA Architecture
- Proxy Service
- Integrated Layer 4 Traffic Monitor
- Data Loss Prevention
- Cisco Cognitive Intelligence
- Management Tools
- Cisco Advanced Web Security Reporting (AWSR) and Third-Party Integration
- Cisco Content Security Management Appliance (SMA)
- Deploying Proxy Services
- Explicit Forward Mode vs. Transparent Mode
- Transparent Mode Traffic Redirection
- Web Cache Control Protocol
- Web Cache Communication Protocol (WCCP) Upstream and Downstream Flow
- Proxy Bypass
- Proxy Caching
- Proxy Auto-Config (PAC) Files
- FTP Proxy
- Socket Secure (SOCKS) Proxy
- Proxy Access Log and HTTP Headers
- Customizing Error Notifications with End User Notification (EUN) Pages
- Utilizing Authentication
- Authentication Protocols
- Authentication Realms
- Tracking User Credentials
- Explicit (Forward) and Transparent Proxy Mode
- Bypassing Authentication with Problematic Agents
- Reporting and Authentication
- Re-Authentication
- FTP Proxy Authentication
- Troubleshooting Joining Domains and Test Authentication
- Integration with Cisco Identity Services Engine (ISE)
- Creating Decryption Policies to Control HTTPS Traffic
- Transport Layer Security (TLS)/Secure Sockets Layer (SSL) Inspection Overview
- Certificate Overview
- Overview of HTTPS Decryption Policies
- Activating HTTPS Proxy Function
- Access Control List (ACL) Tags for HTTPS Inspection
- Access Log Examples
- Understanding Differentiated Traffic Access Policies and Identification Profiles
- Overview of Access Policies
- Access Policy Groups
- Overview of Identification Profiles
- Identification Profiles and Authentication
- Access Policy and Identification Profiles Processing Order
- Other Policy Types
- Access Log Examples
- ACL Decision Tags and Policy Groups
- Enforcing Time-Based and Traffic Volume Acceptable Use Policies, and End User Notifications
- Defending Against Malware
- Web Reputation Filters
- Anti-Malware Scanning
- Scanning Outbound Traffic
- Anti-Malware and Reputation in Policies
- File Reputation Filtering and File Analysis
- Cisco Advanced Malware Protection
- File Reputation and Analysis Features
- Integration with Cisco Cognitive Intelligence
- Enforcing Acceptable Use Control Settings
- Controlling Web Usage
- URL Filtering
- URL Category Solutions
- Dynamic Content Analysis Engine
- Web Application Visibility and Control
- Enforcing Media Bandwidth Limits
- Software as a Service (SaaS) Access Control
- Filtering Adult Content
- Data Security and Data Loss Prevention
- Data Security
- Cisco Data Security Solution
- Data Security Policy Definitions
- Data Security Logs
- Performing Administration and Troubleshooting
- Monitor the Cisco Web Security Appliance
- Cisco WSA Reports
- Monitoring System Activity Through Logs
- System Administration Tasks
- Troubleshooting
- Command Line Interface
- References
- Comparing Cisco WSA Models
- Comparing Cisco SMA Models
- Overview of Connect, Install, and Configure
- Deploying the Cisco Web Security Appliance Open Virtualization Format (OVF) Template
- Mapping Cisco Web Security Appliance Virtual Machine (VM) Ports to Correct Networks
- Connecting to the Cisco Web Security Virtual Appliance
- Enabling Layer 4 Traffic Monitor (L4TM)
- Accessing and Running the System Setup Wizard
- Reconnecting to the Cisco Web Security Appliance
- High Availability Overview
- Hardware Redundancy
- Introducing Common Address Redundancy Protocol (CARP)
- Configuring Failover Groups for High Availability
- Feature Comparison Across Traffic Redirection Options
- Architecture Scenarios When Deploying Cisco AnyConnect® Secure Mobility
- Most important Labs
- Configure the Cisco Web Security Appliance
- Deploy Proxy Services
- Configure Proxy Authentication
- Configure HTTPS Inspection
- Create and Enforce a Time/Date-Based Acceptable Use Policy
- Configure Advanced Malware Protection
- Configure Referrer Header Exceptions
- Utilize Third-Party Security Feeds and MS Office 365 External Feed
- Validate an Intermediate Certificate
- View Reporting Services and Web Tracking
- Perform Centralized Cisco AsyncOS Software Upgrade Using Cisco SMA
Laboratory Activities
- Configure the Cisco Web Security Appliance
- Deploy Proxy Services
- Configure Proxy Authentication
- Configure HTTPS Inspection
- Create and Enforce a Time/Date-Based Acceptable Use Policy
- Configure Advanced Malware Protection
- Configure Referrer Header Exceptions
- Utilize Third-Party Security Feeds and MS Office 365 External Feed
- Validate an Intermediate Certificate
- View Reporting Services and Web Tracking
Course Mode
Instructor-Led Remote Live Classroom Training;
Trainers
Trainers are Cisco Official Instructors and certified in other IT technologies, with years of hands-on experience in the industry and in Training.
Lab Topology
For all types of delivery, the Trainee can access real Cisco equipment and systems in our laboratories or directly at the Cisco data centers remotely 24 hours a day. Each participant has access to implement the various configurations thus having a practical and immediate feedback of the theoretical concepts.
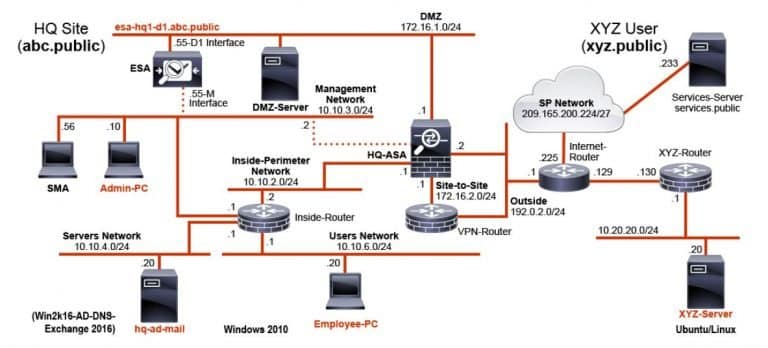
Here are some Cisco Labs network topologies available:
Course Details
Course Prerequisites
Attendance at the Cisco CCNA Course as well as attendance at the Cisco Cybersecurity Course is Course is recommended .
Course Duration
Intensive duration 2 days
Course Frequency
Course Duration: 2 days (9.00 to 17.00) - Ask for other types of attendance.
Course Date
- Cisco SWSA course (Intensive Formula) – On request – 9:00 – 17:00
Steps to Enroll
Registration takes place by asking to be contacted from the following link, or by contacting the office at the international number +355 45 301 313 or by sending a request to the email info@hadartraining.com



