Administering Information Protection and Compliance in Microsoft 365 SC-400

The SC-400 Microsoft Information Protection and Compliance in Microsoft 365 course is designed for participants who want to specialize in information protection and compliance in Microsoft 365. The course explores managing risks associated with corporate information, implementing and managing information protection solutions, and monitoring and responding to threats. Tools such as Microsoft Information Protection, Microsoft 365 Compliance, and Azure Information Protection are used. The course contributes to the preparation of the Microsoft Information Protection and Compliance Administrator Associate Certification exam .
Course Objectives
Below is a summary of the main objectives of the Microsoft Information Protection and Compliance SC-400 Course :
- Implement Microsoft information protection solutions.
- Manage compliance in Microsoft 365.
- Monitor and respond to cyber threats.
- Use Microsoft Information Protection and Microsoft 365 Compliance.
- Apply Azure Information Protection for data security.
- Conduct risk assessments and audits for compliance.
- Integrate compliance solutions with third-party applications.
- Configure data loss prevention (DLP) policies in Microsoft 365.
Course Certification
This course helps you prepare to take the:
EExam SC-400 Microsoft Information Protection and Complianc;
Course Outline
Create and manage sensitive info types
- Identify sensitive information requirements for an organization’s data
- Translate sensitive information requirements into built-in or custom sensitive info types
- Create and manage custom sensitive info types
- Create and manage exact data match (EDM) classifiers
- Implement document fingerprinting
Create and manage trainable classifiers
- Identify when to use trainable classifiers
- Design and create a trainable classifier
- Test a trainable classifier
- Retrain a trainable classifier
Implement and manage sensitivity labels
- Implement roles and permissions for administering sensitivity labels
- Define and create sensitivity labels
- Configure and manage sensitivity label policies
- Configure auto-labeling policies for sensitivity labels
- Monitor data classification and label usage by using Content explorer, Activity explorer, and audit search
- Apply bulk classification to on-premises data by using the Microsoft Purview Information Protection scanner
- Manage protection settings and marking for applied sensitivity labels
Design and implement encryption for email messages
- Design an email encryption solution based on methods available in Microsoft 365
- Implement Microsoft Purview Message Encryption
- Implement Microsoft Purview Advanced Message Encryption
Create and configure DLP policies
- Design DLP policies based on an organization’s requirements
- Configure permissions for DLP
- Create and manage DLP policies
- Interpret policy and rule precedence in DLP
- Configure a Microsoft Defender for Cloud Apps file policy to use DLP policies
Implement and monitor DLP endpoints
- Configure advanced DLP rules for devices in DLP policies
- Configure Endpoint DLP settings
- Recommend a deployment method for device onboarding
- Identify endpoint requirements for device onboarding
- Monitor endpoint activities
- Implement the Microsoft Purview Extension
Monitor and manage DLP activities
- Analyze DLP reports
- Analyze DLP activities by using Activity explorer
- Remediate DLP alerts in the Microsoft Purview compliance portal
- Remediate DLP alerts generated by Defender for Cloud Apps
Retain and delete data by using retention labels
- Plan for information retention and disposition by using retention labels
- Create retention labels for data lifecycle management
- Configure and manage adaptive scopes
- Configure a retention label policy to publish labels
- Configure a retention label policy to auto-apply labels
- Interpret the results of policy precedence, including using Policy lookup
Manage data retention in Microsoft 365 workloads
- Create and apply retention policies for SharePoint and OneDrive
- Create and apply retention policies for Microsoft 365 groups
- Create and apply retention policies for Teams
- Create and apply retention policies for Yammer
- Create and apply retention policies for Exchange Online
- Apply mailbox holds in Exchange Online
- Implement Exchange Online archiving policies
- Configure preservation locks for retention policies and retention label policies
- Recover retained content in Microsoft 365
Implement Microsoft Purview records management
- Create and configure retention labels for records management
- Manage retention labels by using a file plan, including file plan descriptors
- Classify records by using retention labels and retention label policies
- Manage event-based retention
- Manage the disposition of content in records management
- Configure records management settings, including retention label settings and disposition settings
Plan and manage regulatory requirements by using Microsoft Purview Compliance Manager
- Plan for regulatory compliance in Microsoft 365
- Create and manage assessments
- Create and modify custom templates
- Interpret and manage improvement actions
- Create and manage alert policies for assessments
Plan and manage eDiscovery and Content search
- Choose between eDiscovery (Standard) and eDiscovery (Premium) based on an organization’s requirements
- Plan and implement eDiscovery
- Delegate permissions to use eDiscovery and Content search
- Perform searches and respond to results from eDiscovery
- Manage eDiscovery cases
- Perform searches by using Content search
Manage and analyze audit logs and reports in Microsoft Purview
- Choose between Audit (Standard) and Audit (Premium) based on an organization’s requirements
- Plan for and configure auditing
- Investigate activities by using the unified audit log
- Review and interpret compliance reports and dashboards
- Configure alert policies
- Configure audit retention policies
Implement and manage Microsoft Purview Communication Compliance
- Plan for communication compliance
- Create and manage communication compliance policies
- Investigate and remediate communication compliance alerts and reports
Implement and manage Microsoft Purview Insider Risk Management
- Plan for insider risk management
- Create and manage insider risk management policies
- Investigate and remediate insider risk activities, alerts, and reports
- Manage insider risk cases
- Manage forensic evidence settings
- Manage notice templates
Implement and manage Microsoft Purview Information Barriers (IBs)
- Plan for IBs
- Create and manage IB segments and policies
- Configure Teams, SharePoint, and OneDrive to enforce IBs, including setting barrier modes
- Investigate issues with IB policies
Implement and manage privacy requirements by using Microsoft Priva
- Configure and maintain privacy risk management
- Create and manage Privacy Risk Management policies
- Identify and monitor potential risks involving personal data
- Evaluate and remediate alerts and issues
- Implement and manage subject rights requests
Course Mode
Instructor-Led Remote Live Classroom Training;
Trainers
Trainers are authorized Instructors in Microsoft and certified in other IT technologies, with years of hands-on experience in the industry and in Training.
Lab Topology
For all types of delivery, the participant can access the equipment and actual systems in our laboratories or directly in international data centers remotely, 24/7. Each participant has access to implement various configurations, Thus immediately applying the theory learned. Below are some scenarios drawn from laboratory activities.
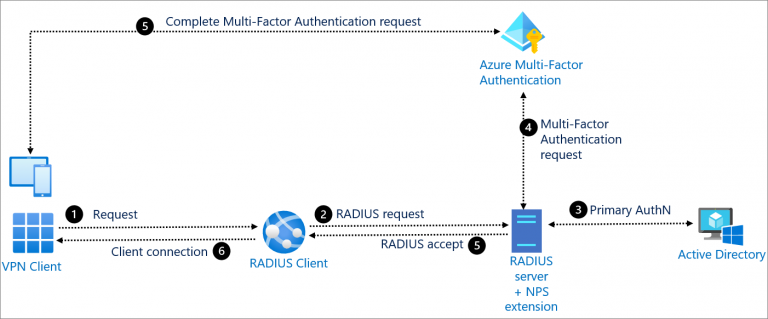
Course Details
Course Prerequisites
- Attendance at the Microsoft Security, Compliance, and Identity Fundamentals Course (SC-900) is recommended .
Course Duration
Intensive duration :2 days;
Course Frequency
Course Duration: 2 days (9.00 to 17.00) - Ask for other types of attendance.
Course Date
- Administering Information Protection and Compliance in Microsoft 365 Course (Intensive Formula) – On request – 09:00 – 17:00
Steps to Enroll
Registration takes place by asking to be contacted from the following link, or by contacting the office at the international number +355 45 301 313 or by sending a request to the email info@hadartraining.com


